Others - Assimilator

Title:『 Portrait2020_2011re-edition 』
Year:2019
Material:silicone, metal, plastic, motor, software, MCU, sensors, water tank, junks
Size:Size variable
“cRying behind you”,

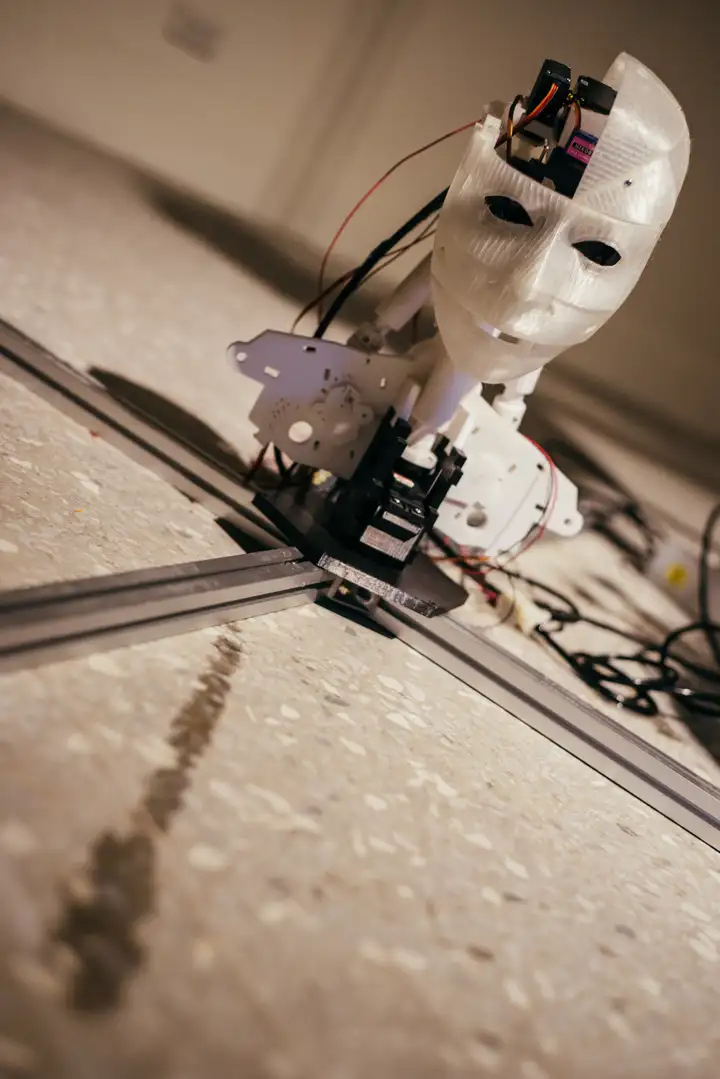
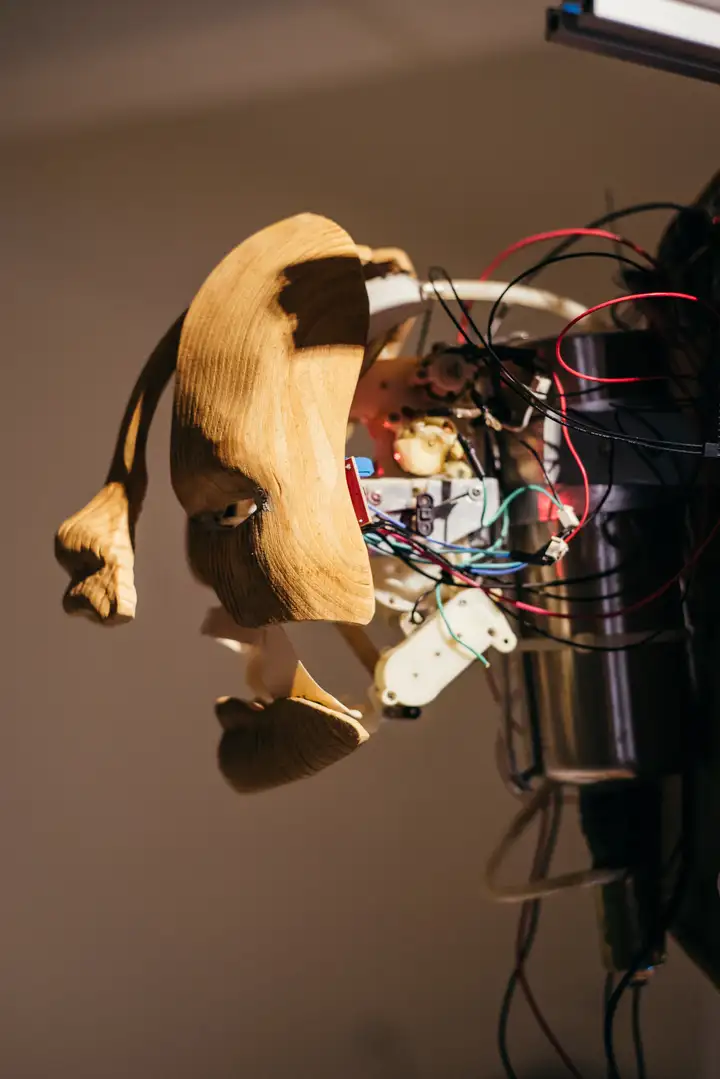
The installation is a robotic head. When there are people in the exhibition space, it will be move and react with some facial expressions, but when there is no one in the space, it will bow its head and cry.
In the beginning, around 2010, when thinking about artificial intelligence and robotic design, I thought that if I brought only one of the human emotions and behaviour into a simple mechanical object and find a way to increase emotion by certain behaviour. So bringing the crying into a robotic head, and make it only cry when nobody around.
Happy, sad or strong emotions which cause the biological behaviour
, "cry", but some people will hide strong emotions behind people and do not want to be seen.
開心、傷心或強烈情緒會讓人有哭泣的行爲,但有些人會將倔強、脆弱等多重情緒隱藏其後,不希望讓人看見背後深沉的一面,於是「在你背後哭泣」(Crying behind your back)成為這件作品最直觀的概念:展場中的機械人頭,會對觀眾產生細微的動作與表情的反應,但遇空無一人時,它便會低頭哭泣。
2010年因思考人工智慧與機器人情緒認知的問題,於是嘗試賦予機械有了情緒,並且用人類哭泣的行為強化情緒動機。本作品集結2010年至今的系列實驗創作,並呼展覽空間的環境機能,類人體的循環系統流淌漫延於作品四周。
Title:『 Invitation 』
Year:2016
Material:scripts、e-invitation
Size:Size variable
This work is similar to malware, by sending exhibition invitations to infect the client's computer. By kidnapping the browser, the inviter's computer will appear a simple infection screen from time to time, but it will not affect its daily use. It is a re-edition of 2019 because the system and browser security are more secure nowadays, so it is different from the original work.
Computer viruses and malware have used extreme methods to force system monopolies to update security and improve the system environment in history. But also used by criminal as a method to steal confidential business and personal information. In the form of an exhibition invitation letter, the inviter's email client is used to generate the works in the work.
在電腦病毒史上,惡意軟體最初是以極端方式滲透電腦系統,威脅企業更新安全性及改善系統環境,因此也讓不肖份子作為竊取商業與個人機密資料的手段。挪用這樣的概念,〈Invitation〉作品類似惡意軟體,藉由發送展覽邀請函,受邀者開啟邀請函後,受邀者電腦將不定時出現感染畫面,但不影響其他使用功能。因系統與瀏覽器安全性的更新,本作品為2019年再製版。
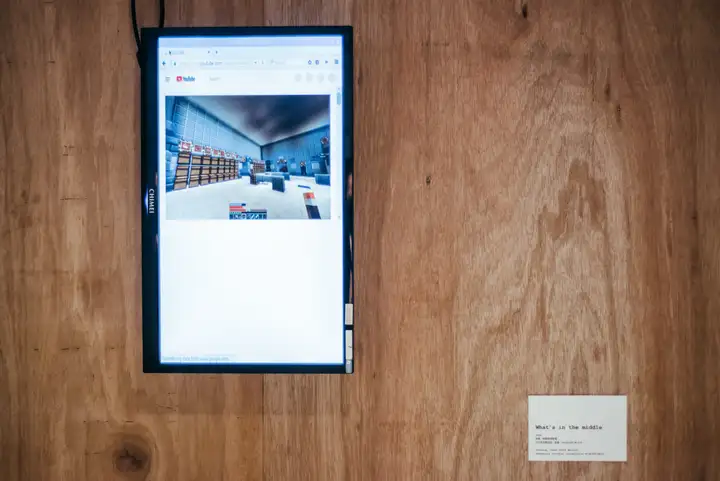
Title:『 What’s in the middle 』
Year:2018
Material:software、radio sniff devices
Size:Size variable
The work intercepts network packets in different domains, network, and decodes them, mixes the content of the packets to generate/render new contents.
Internet as an extension of human perception, when users surfing the internet in a certain area will continuously send and receive network packets, this work is keeping to decode network packets and converted into a format that browsers can read. The user's digital footprint in a specific domain will be restricted by the "MITM" and parsing insecure packets, and the error data generated by the hybrid imaging method and the forced dump from the packets. To visualize and display the result as an abstract image, so "WHat's in the middle?"
今日的網路作為現代人感知器官的延伸,在一定區域內的網路使用者會不斷發送、以及接收網路加密後的複雜資訊。作品〈What’s in the middle〉的發想由此而生,藉由解碼(decode)網路封包,並轉為瀏覽器可讀取的格式,將特定網域內的使用者足跡顯示給觀眾。這種由中間人攻擊(Man-in-the-middle attack)攔截與解析未加密封包的混合成像作法,強制轉儲(dump)加密封包而產生的錯誤資料,透過去視覺化與顯示較為抽象的圖像,我們將會在螢幕上看到什麼呢?(WHat’s in the middle?)